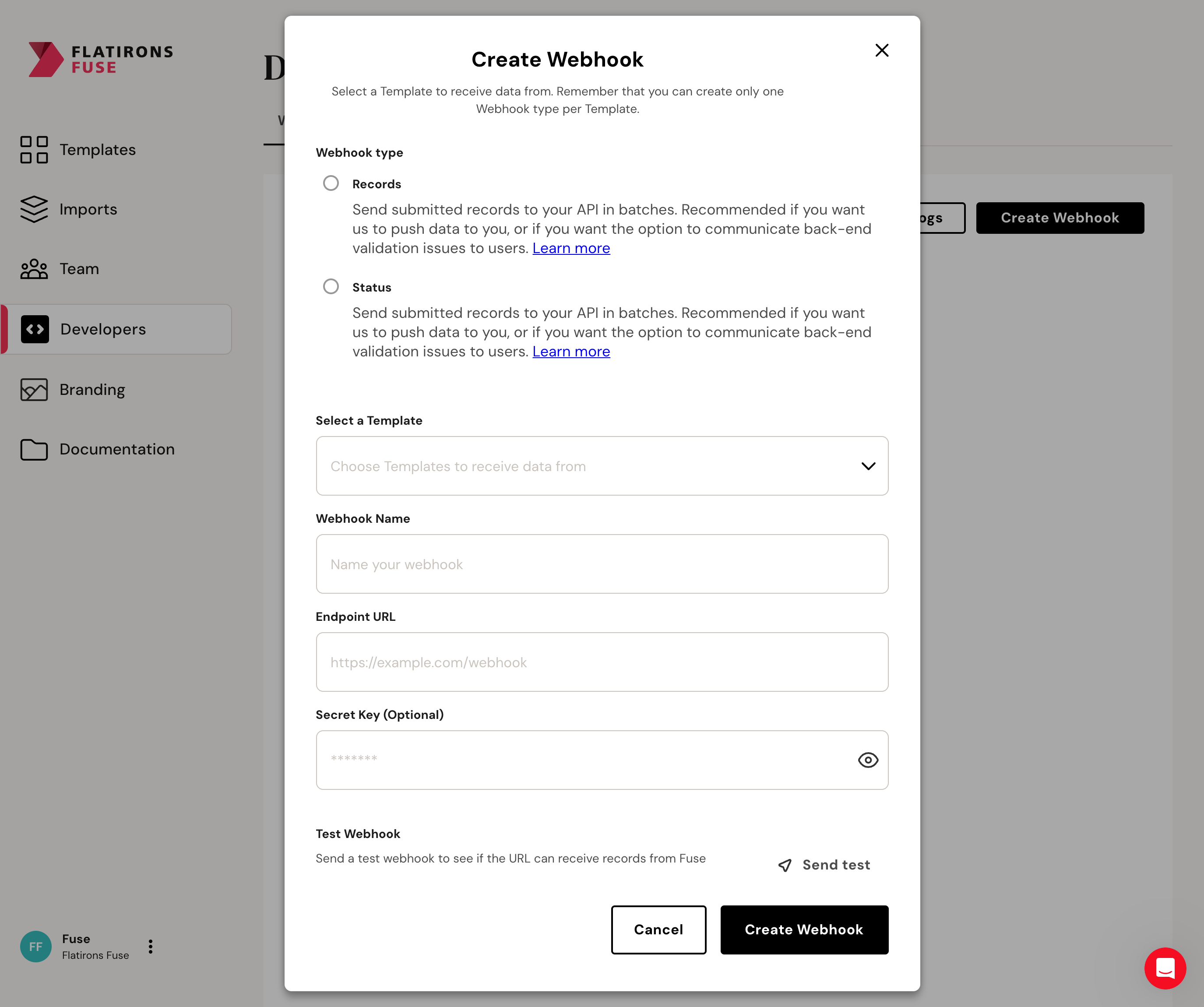
 To add a Webhook, go to the Developers tab of your Fuse account.
To add a Webhook, go to the Developers tab of your Fuse account.
Accessing Data
Webhook Security
Learn how to implement signature verification for secure communication with webhooks
When creating webhooks, you have the option to provide a secret key for added security. This secret key is used to generate a signature for each outgoing payload. To ensure the integrity of incoming webhook payloads, you can validate the signature on your server.
 To add a Webhook, go to the Developers tab of your Fuse account.
To add a Webhook, go to the Developers tab of your Fuse account.
 To add a Webhook, go to the Developers tab of your Fuse account.
To add a Webhook, go to the Developers tab of your Fuse account.
⌘I

